Web Application Security
Web apps are one of the most widely used types of software nowadays. Web applications pose a unique challenge to any organisation’s security posture due to their complexity and pervasiveness. Because modern online apps handle more sensitive data, they have to be protected from being a substantial hazard to an organisation.
Our Web App Security Services Include
Dotsquares employs a skilled team of certified penetration testers who focus on online application penetration testing. Our penetration testing team is varied, with extensive security and software development experience. We are incredibly capable of pen-testing web applications, web services, APIs, and other technologies across a wide range of technologies
The security of a web application is very critical for your organisation or business. A web application penetration service tests the vulnerabilities in the architecture and configuration of the app. To prevent data exposure and unauthorised access, you have to stay prepared with security. Vulnerabilities in the web app are different from common network vulnerabilities. A web app interacts with many users regularly, which is why it is an easy target for malicious attackers. With our foolproof services, your business will be secured from every cyber threat, and you can run web applications smoothly.
Our security experts will monitor the web app and analyse patterns of attacks with regular scanning to take precise steps to avoid any data breach.
Don’t Postpone Web Application Penetration Testing for Tomorrow
Get in Touch Today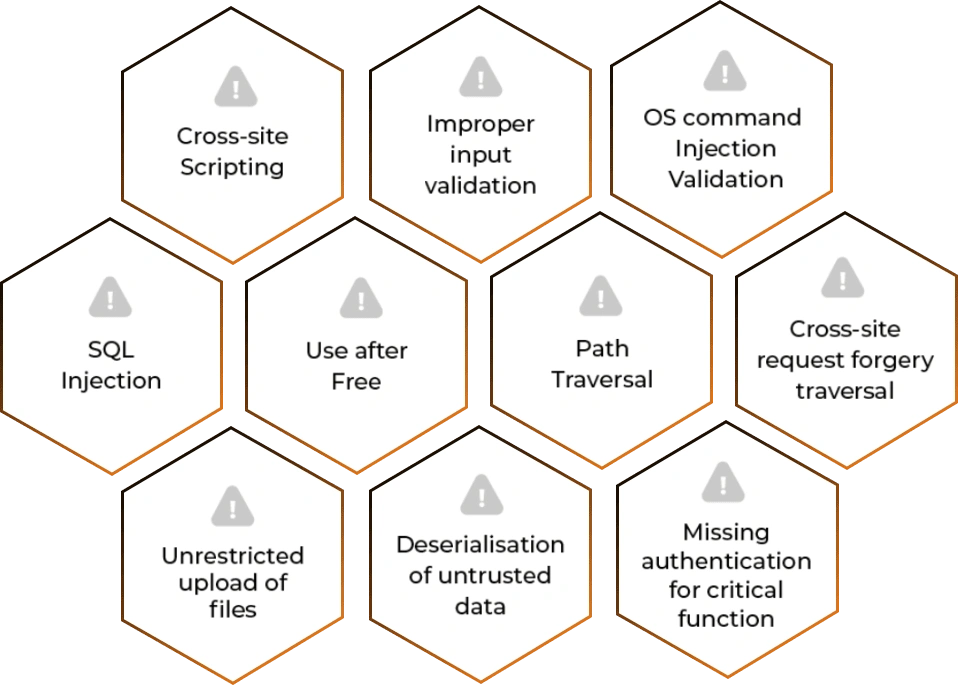
Top 10 Most Common Web Application Vulnerabilities
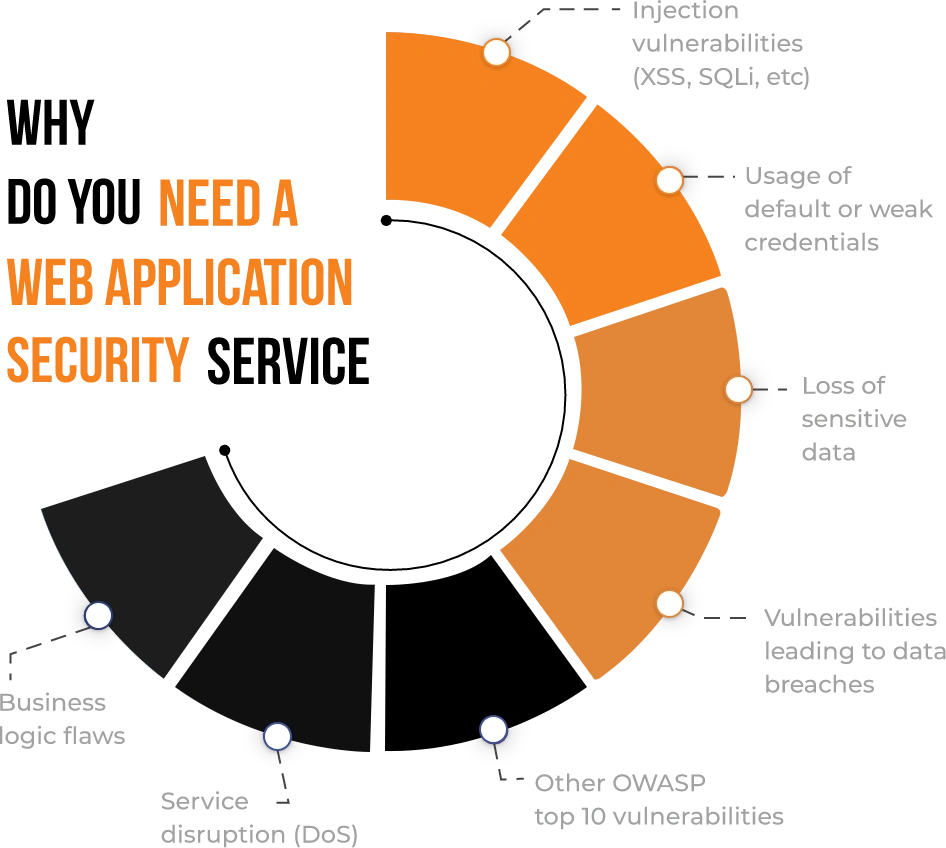
In today’s world, a web application might be overwhelmed by a wide range of challenges. Web Applications linger with common security misconfigurations and vulnerabilities. Several of the top attacks employed by attackers can cause significant harm to an individual application or the entire organisation using these vulnerabilities. Knowing the assaults that make an application vulnerable, as well as the probable results of an attack, allows your company to resolve problems in advance and effectively test for them.
We can keep you away and safe from DDoS, XSS, SQLi, clickjacking, and other security misconfigurations, as well as every other potential attack that your web application might face.
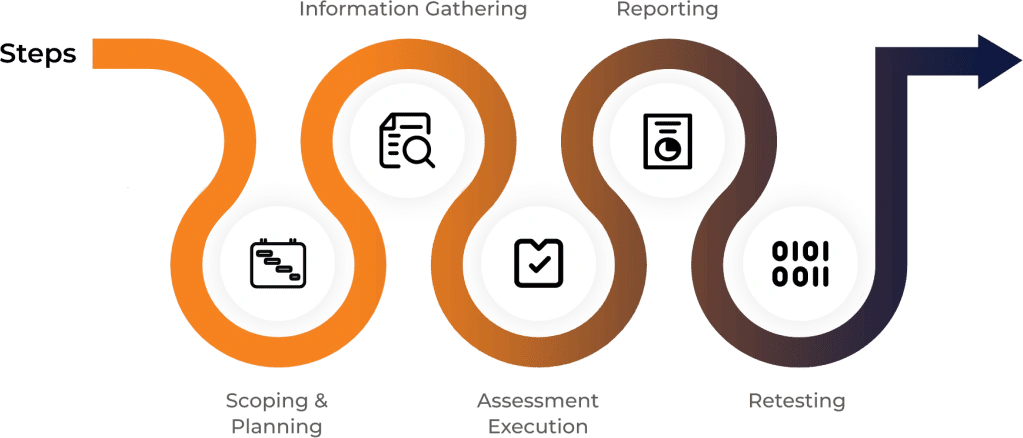
Our Assessment Methdology
A holistic approach to perform penetration test that not only discovers security vulnerabilities, but also finding business logic vulnerabilities along with security checklists based on industry standards, including OWASP Top 10, PCI Compliance etc.

Before initiating an assessment, Dotsquares establishes a well-defined scope with the client. At this stage, we encourage open communication between our team and the client organization to lay a solid foundation for the upcoming assessment.

Consultants at Dotsquares utilize a wide array of OSINT (Open Source Intelligence) methods and tools to accumulate extensive information about the target. This gathered data aids in comprehending the operational states of the organization, enabling us to accurately assess the risk as the engagement unfolds.

At this point, we gather our custom scripts and tools, along with other advanced methods for more sophisticated data collection. Dotsquares specialists meticulously validate all potential attack vectors. The information gathered during this phase lays the foundation for further exploitation in the subsequent stage.

In this phase, we kick-start a combination of manual and automated inspections to identify potential attack vectors and vulnerabilities. Following this, we carry out exploitation to offer proof-of-concepts. We employ a variety of techniques, including open-source and bespoke tools during this stage. All these procedures are executed meticulously to avoid any disruption to your business operations.

This marks the culmination of the entire assessment. At this juncture, the experts at Dotsquares consolidate all gathered data and deliver the client with an exhaustive, detailed report of our findings. This comprehensive document will include an overarching analysis of all identified risks, while spotlighting both the strengths and weaknesses inherent in the application.

After the process is finished, our team will review the report and identify suitable solutions for any detected bugs. Subsequently, an in-depth discussion will take place to address these vulnerabilities. We’ll make certain that all modifications have been correctly implemented and all vulnerabilities are resolved. The team will deliver a thorough remediation or closure report, demonstrating the enhanced security status of the application.
Track and Manage Web Application Security Risks and Progress with Industry Experts
Contact Us NowWhat we have done
Explore some of our projects showcasing our expertise in creating robust and scalable solutions.
Tailored Technologies to Conquer Your Development Challenges
Harness the power of our advanced technologies to elevate user interaction and drive engagement.
The Advantages of Working with Dotsquares for Development
We craft solutions that transform your business. Here's what sets us apart:
Competitive Rates
Our rates are highly competitive, ensuring that you receive excellent value for your money. With us, you can be confident that you are getting the best possible rates without compromising on quality.
Quality
We take pride in delivering exceptional results. Our CMMI level 3 appraisal and membership in the Agile Alliance demonstrate our commitment to strong processes and quality control. This ensures you get a polished, high-quality product every single time.
In-House Expertise
Our 1,000+ designers, developers, and project managers are all directly employed by us and work in our own offices across the US, UK, India, and globally. This ensures seamless collaboration and control over your project.
Security & Confidentiality
Unlike many offshore companies, security is our top priority. Your data and intellectual property remain completely confidential, and all source code rights belong to you, always.
On-Time Delivery
We use cutting-edge project management tools and agile development practices to keep your project on track. This means you'll get high-quality products delivered exactly when you expect them.

Flexible Engagement Models
We understand that your needs can change. That's why we offer flexible engagement options. Choose the model that works best for you now, and switch seamlessly if your needs evolve. We're committed to building a long-term, reliable partnership with you.
Get Our Assistance for Your Business Needs
At Dotsquares, we provide flexible options for accessing our developers' time, allowing you to choose the duration and frequency of their availability based on your specific requirements.

When you buy bucket hours, you purchase a set number of hours upfront.
- Your purchased bucket hours remain valid for 6 months, during this time frame, you can utilize our services until your hours are exhausted or until the 6-month period expires.
- For example, if you invest in 40 bucket hours and use 10 hours within the first month, you will have a remaining 30 hours to utilize over the next 5 months.
- In this case, the developer will work for other projects simultaneously as you have opted for bucket hours and not dedicated hiring.
It's a convenient and efficient way to manage your developer needs on your schedule.
Explore more
In dedicated hiring, the number of hours are not fixed like the bucket hours but instead, you are reserving the developer exclusively for your project.
- The developer will work only on your project for a set amount of time.
- You can choose to hire the developer for a week or a month, depending on what your project needs.
- This means our developer will focus exclusively on meeting the needs of your project, without any distractions from other commitments.
Whether you need help for a short time or a longer period, our dedicated hiring option ensures your project gets the attention it deserves.
Explore moreOur Agile Development Process
Companies employ developers from us because we have a proven track record of delivering high-quality projects on time.
Planning & Consultation
Our journey begins with understanding your vision. Based on your vision, we collaboratively create a project roadmap with clear milestones. We’ll consult about your ideas, target audience, and desired outcomes.
Initiate discussions to understand your objectives, target audience, and desired outcomes.
Collaboratively create a detailed project plan with clear milestones and deadlines.
Outline the key features, functionalities, and requirements.
Allocate team roles, tools, and budgets to ensure effective project management.
Design
Our skilled designers translate your vision into a user-friendly and visually appealing solution. They focus on creating a positive user experience that keeps users engaged and coming back for more.
Develop wireframes to outline the structure and layout.
Craft the user interface and user experience, focusing on aesthetics and functionality.
Create interactive prototypes for user feedback and refinement.
Present the design for your review and approval, making necessary adjustments based on feedback.
Development
Our expert developers take your design and turn it into reality. We keep you informed throughout the process with regular progress reports and milestone deliverables. This ensures you have complete transparency and control over the development phase.
Code the client-side interface, ensuring responsiveness and compatibility.
Build the server-side logic, integration, and functionalities.
Provide progress reports and milestone deliverables to keep you informed.
Conduct initial testing and debugging to ensure the development functions as intended.
Testing
Before launch, our dedicated QA specialists meticulously test every aspect of your product. They identify and fix any potential issues to guarantee a smooth and flawless user experience.
Test all features and functionalities to ensure they work correctly.
Evaluate the user interface and user experience for ease of use and navigation.
Assess the speed, load time, and responsiveness under various conditions.
Conduct thorough security checks to identify and fix vulnerabilities.
Deployment
Once everything is finalised, our team strategically chooses the most suitable deployment methods and services. Now, your project is live for everyone to see and interact with!
Recommend and set up the most suitable services based on your needs.
Perform final checks and configurations before going live.
Develop a launch plan, including marketing and promotional strategies.
Deploy the product, ensuring everything is functional and optimised for performance.
Maintenance
Our commitment doesn't end at launch. We provide ongoing support to ensure your product stays up-to-date, secure, and bug-free.
Implement software and security updates to keep the website current.
Continuously monitor performance and security to prevent issues.
Address any technical issues or bugs that arise post-launch.
Optimise speed and functionality based on user feedback and analytics.
Launch a value-adding Software Integration Solutions that Drives Your Success
Connect with our experts!
Built Relationships with 15,000+ Happy Clients!
Companies employ software developers from us because we have a proven track record of delivering high-quality projects on time.

5+ Years of Average Experience

Integrity & Transparency

FREE No Obligation Quote

ISO 27001 Information Security

Outcome-Focused Approach

Transparency is Guaranteed

Focus on Security

4.8/5 Rating on Clutch

Hire a Team of Your Choice

Costs Lower Than Your Local Guy

From Challenges to Triumphs
Be inspired by our clients' journeys as we overcome challenges and achieve success together.
Shieldpay Tom Squire
I have worked with Dotsquares for a year now on an instant digital, escrow payment solution. Their team is exceptional and efficient in every manner. It's great to have technology partners who deliver ahead of timelines. I am pleased with their work and performance.


Nick
Director at insidelines.com.au

Tom Squire
Shieldpay

Mark Osmond
Mood Addict.com

Matt Brown
Magical Maths Club
We're here to answer all your questions.
Once you book a consultation, our experts contact you within 24 hours to discuss your needs. We define the testing scope, gather necessary information, and conduct a thorough assessment tailored to your requirements.
Our services protect your digital assets from various cyber threats, ensuring smooth operation, preventing data breaches, financial losses, and reputational damage. We identify and mitigate vulnerabilities to keep your business secure and resilient.
The assessment duration depends on your application's complexity. After an initial consultation, we provide a tailored timeline and can start assessments promptly to address any urgent security needs.
Our penetration testing is designed to minimize disruption. We operate in a controlled environment and follow strict protocols, ensuring the assessment does not impact your live systems or business operations.
Yes, we offer ongoing monitoring to identify new vulnerabilities and provide continuous support, ensuring your web application's security posture remains strong and up-to-date against emerging threats.


















































































